Caesar Cipher Tool
Securely encode and decode messages using the ancient Caesar cipher technique
Input
Output
To encode: Enter text, set shift value, click "Encode"
To decode: Enter encoded text, use same shift value, click "Decode"
Secure Encryption
Uses the same method Julius Caesar used for military communications.
Custom Shifts
Choose any shift value from 1 to 25 for your cipher.
Easy Copy
One-click copy for your encoded/decoded messages.
Responsive
Works perfectly on all devices from desktop to mobile.
The Caesar Cipher: Unveiling the Secrets of Ancient Encryption Power
Meta Description: The Caesar Cipher, one of the oldest encryption techniques, showcases the foundations of cryptography and its timeless influence on modern security systems.
I. Introduction
A. What Is the Caesar Cipher?
The Caesar Cipher is one of the simplest and most well-known encryption techniques in history. It operates by shifting each letter in a message by a fixed number of positions within the alphabet. For example, shifting every letter by three turns “HELLO” into “KHOOR.” This fundamental method introduces the concept of substitution ciphers, where each letter is replaced with another according to a set rule.
B. Why It Matters in the History of Cryptography
The Caesar Cipher represents the dawn of cryptography — the art and science of keeping messages secret. Though it’s easily broken by modern standards, it was a revolutionary idea in ancient times. It allowed military leaders, particularly Julius Caesar himself, to send confidential information without fear of interception.
C. The Timeless Appeal of Simple Encryption
Even today, this simple cipher remains a favorite among students, educators, and programmers. It serves as a gateway into the world of data protection and digital encryption. Despite being “cracked,” its conceptual elegance continues to inspire cryptographers and enthusiasts alike.
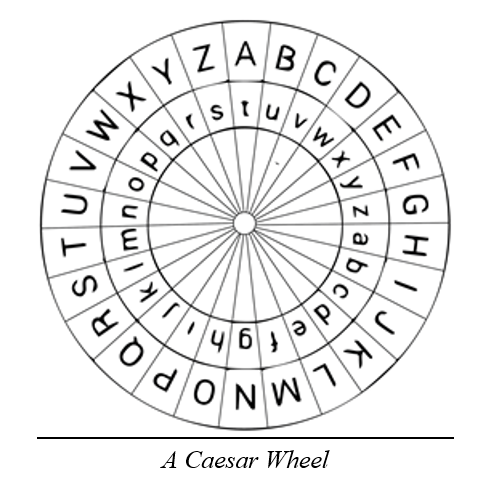
II. The Origins of the Caesar Cipher
A. Historical Context: The Roman Empire and Julius Caesar
During the height of the Roman Empire, secure communication was vital for military strategy. Julius Caesar reportedly used his namesake cipher to send messages to his generals, ensuring that enemies could not easily interpret them if intercepted.
B. The Purpose of the Cipher in Ancient Military Communication
The main advantage of the Caesar Cipher was its simplicity. Caesar’s soldiers could easily memorize and apply it in the field. By shifting the alphabet by three letters, they maintained a basic yet effective method of secrecy.
C. Early Documentation and Examples
The first references to the Caesar Cipher come from ancient historians like Suetonius, who detailed Caesar’s use of encoded messages. These examples highlight the early understanding of secrecy as a tactical advantage, centuries before the birth of modern cryptography.
III. The Core Principle of the Cipher
A. The Concept of Substitution Ciphers
At its heart, the Caesar Cipher belongs to the family of substitution ciphers — systems where each letter of the plaintext is replaced with another symbol or letter. This concept laid the groundwork for complex cryptographic systems.
B. How the Caesar Cipher Shifts the Alphabet
When using a shift of 3:
- A → D
- B → E
- C → F
…and so on.
Once the alphabet reaches Z, it wraps back to A.
C. The Mathematical Formula Behind the Cipher
Mathematically, the Caesar Cipher can be expressed as:
E(x) = (x + n) mod 26
Where:
- E(x) is the encrypted letter,
- x is the original letter’s position,
- n is the shift value,
- mod 26 ensures the wraparound.
D. Case Study: Shifting by 3 – Caesar’s Classic Example
If we take the message “Veni, Vidi, Vici” and shift it by 3:
- V → Y
- E → H
- N → Q
- I → L
Resulting in “Yhql, Ylgl, Ylfl.”
Simple, yet remarkably effective in its time.
IV. Implementing the Caesar Cipher
A. Step-by-Step Encryption Process
- Choose a shift value (e.g., 3).
- Replace each letter with one that is three places ahead.
- Preserve spaces and punctuation.
- The result is your ciphertext.
B. Decryption: Reversing the Shift
To decrypt, simply reverse the process:
D(x) = (x – n) mod 26
So shifting backward by 3 restores the original message.
C. Handling Edge Cases (Non-Letters, Numbers, and Punctuation)
Modern implementations typically ignore symbols and punctuation, encrypting only letters to preserve readability.
D. Caesar Cipher with Uppercase and Lowercase Letters
While the original Roman alphabet didn’t distinguish cases, modern versions maintain both uppercase and lowercase mappings for convenience.
V. Manual vs. Automated Encryption
A. Hand Encoding Techniques
Before computers, encoding was performed using alphabet wheels or written tables. Soldiers and scholars often carried such tools for quick reference.
B. Modern Computational Methods
Today, Caesar Cipher encryption can be executed instantly using software, mobile apps, or online tools. These automate both encryption and decryption seamlessly.
C. Using Programming Languages to Implement the Cipher (Python Example)
Here’s a simple Python implementation:
def caesar_cipher(text, shift):
result = ""
for char in text:
if char.isalpha():
base = ord('A') if char.isupper() else ord('a')
result += chr((ord(char) - base + shift) % 26 + base)
else:
result += char
return result
VI. The Mathematics of the Caesar Cipher
A. Modular Arithmetic Explained
The Caesar Cipher relies on modular arithmetic, ensuring that when letters reach the end of the alphabet, they loop back to the start.
B. The Role of ASCII Codes
Computers process text as numerical ASCII values. Using these codes allows algorithms to shift letters efficiently during encryption and decryption.
C. How the Cipher Fits into Modular Operations
The modular operation (x + n) mod 26 ensures the continuity of the alphabet, creating a perfect circular encryption system.
VII. Security Analysis
A. The Strength and Weaknesses of Simple Substitution
The cipher’s simplicity is both its strength and its downfall. While easy to understand, it offers minimal resistance against decryption attempts.
B. Brute Force Attacks: Trying All 25 Keys
Because there are only 25 possible shifts, modern computers (or even humans) can decrypt it by testing all options.
C. Frequency Analysis and Cryptanalysis Techniques
By analyzing letter frequency — for instance, recognizing that E is the most common letter in English — attackers can quickly uncover the shift.
D. Why the Cipher Is Considered “Broken” Today
Given today’s computational power and analytical tools, the Caesar Cipher no longer provides true security, though it remains educationally invaluable.
VIII. Variations and Extensions
A. ROT13 and Its Use on the Internet
ROT13 is a modern adaptation that shifts letters by 13 positions. It’s used online for hiding spoilers, jokes, or mild obfuscation.
B. Multiple Shift Ciphers
Advanced systems applied different shifts to different letters, increasing complexity and reducing predictability.
C. Polyalphabetic and Transposition Variants
These variants introduced multiple alphabets or rearranged characters, making them harder to decode.
D. Relationship to the Vigenère Cipher
The Vigenère Cipher evolved from Caesar’s method, using a keyword-based shifting pattern for stronger encryption.
