Eighteen months after a significant cyber incident in which a whole bunch of organisations had been victimised by a ransomware gang that exploited a zero-day SQL injection vulnerability in Progress Software’s MOVEit Transfer file switch product, a number of new victims have come to light, together with tech large Amazon, which has confirmed that data on greater than two million of its staff has been leaked.
CVE-2023-34362 is a important zero-day SQL injection vulnerability in the MOVEit Transfer software, which was patched at the end of May 2023, however sadly not earlier than the Cl0p/Clop ransomware operation was in a position to use it to orchestrate a mass breach of organisations worldwide.
Victims in the UK included the BBC, Boots and British Airways – all of which had been compromised via payroll and human resources IT specialist Zellis.
This week, researchers at Hudson Rock published details of a major data leak affecting no less than 25 organisations, orchestrated by an actor utilizing the deal with Nam3L3ss, who posted them to an underground cyber felony discussion board in CSV format.
According to Hudson Rock’s Alon Gal, the data consists of worker data from main firms together with HP, HSBC, Lenovo, Omnicom, Urban Outfitters, British Telecom and McDonalds, however by some margin the most important tranche of data – a complete of over 2.8 million data – has come from Amazon.
Gal mentioned the dataset included contact data and data on organisational roles and departmental assignments inside Amazon, which might put staff liable to social engineering and tailor-made phishing attacks.
“Hudson Rock researchers had been in a position to confirm the authenticity of the data by cross-referencing emails from the leaks to Linkedin profiles of staff, and to emails discovered in infostealer infections the place staff in the affected firms had been concerned,” wrote Gal.
In a press release circulated to media, Amazon senior PR supervisor Adam Montgomery confirmed the veracity of the breach.
“We had been notified a few safety occasion at one in every of our property administration distributors that impacted a number of of its clients together with Amazon. The solely Amazon data concerned was worker work contact data, for instance work e-mail addresses, desk cellphone numbers, and constructing places,” mentioned Montgomery.
“Amazon and AWS techniques stay safe and we have now not skilled a safety occasion,” he mentioned.
Amazon didn’t identify the organisation by which it was affected.
Link to Cl0p?
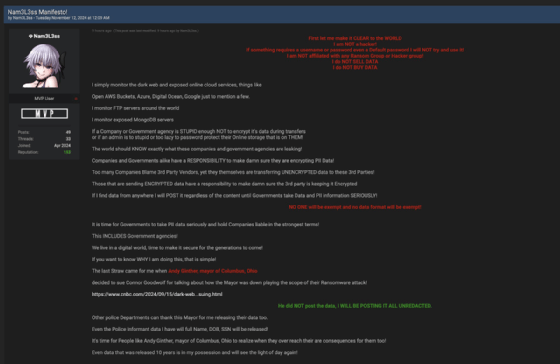
In screenshots of posts made by Nam3Less, shared with Computer Weekly by researchers at Searchlight Cyber, the actor claimed they had been neither a hacker nor affiliated with any ransomware group. They additionally mentioned they didn’t purchase or promote data, slightly they monitored the darkish internet and different uncovered providers together with AWS Buckets, Azure Blobs, MongoDB servers and the like.
“If an organization or authorities company is silly sufficient not to encrypt its data throughout transfers or if an admin is simply too silly or too lazy to password defend their on-line storage that’s on them,” mentioned Nam3L3ss. “The world ought to know precisely what these firms and authorities companies are leaking.”
Whether or not Nam3L3ss has any hyperlink to the Cl0p ransomware gang is unclear and has not but been confirmed. Despite their very own assertions, statements made by menace actors ought to at all times be handled sceptically. Nam3L3ss might simply be an affiliate or affiliate of the gang, however it’s equally attainable that they got here by the data by way of different means.
“The actor Nam3L3ss claims that they don’t seem to be a hacker and that they’re solely sharing data that they’ve downloaded from different sources. As you possibly can see from the assertion that they shared on BreachForums on Tuesday November 12 2024, they declare to be motivated not by monetary achieve, however out of a need to maintain governments and companies accountable for shielding citizen data,” mentioned Searchlight menace intelligence analyst Vlad Mironescu.
“One supply of data that the actor generally makes use of is data that has been posted on ransomware leak websites. For instance, loads of the data Nam3L3ss shares, together with this Amazon data, seems to come from victims of the MOVEit attacks from final 12 months, which was orchestrated by the ransomware group Cl0p. Nam3L3ss doesn’t seem to be related to Cl0p or any ransomware group however is solely resharing the data they’ve discovered.”
Mironescu continued: “It is true that the actor will not be promoting this data, they’re posting it free of charge or for in-forum credit. However, that doesn’t imply there is no such thing as a harm achieved; posting the data free of charge in BreachForums will put it into the arms of a lot of hackers who might use it for all kinds of nefarious functions.”
Dark internet
Kevin Robertson, chief working officer at Acumen Cyber, mentioned: “This leak exhibits how data makes its manner throughout the darkish internet, usually reappearing in the information lengthy after breaches befell and infrequently in the arms of different attackers.
“The MOVEit breach dominated headlines final 12 months after it impacted 1000’s of organisations and billions of peoples’ data. It was one of many first examples of a worldwide provide chain assault that obtained so giant even its perpetrators, Cl0p, struggled to ingest the quantity of data compromised.
“The assault hasn’t had wherever close to the media protection this 12 months because it acquired final 12 months, however this newest replace exhibits that attackers are persevering with to monetise from the data. Nam3L3ss will not be thought to be part of the preliminary MOVEit assault, however a few of its data has landed in their arms, which gives proof of how stolen data is marketed throughout the darkish internet,” he mentioned.